Maybe the most important word in crypto – security – is its one aspect that most often remains overlooked, and users continue to fall victim to their own negligence and lack of knowledge. In reality, following several simple rules is sufficient to secure your digital holdings, and it all starts with choosing the right crypto wallet for your needs. It doesn’t end there, however – protecting your funds is a continuous process, as many crypto horror stories prove.
Half of all ICOs in 2017 are now non-existent projects, as reported by Fortune. Scams have and continue to run rampant, and nearly 80% of all ICOs for 2017 were, in fact, operated by scammers, CoinTelegraph says. Hacks, as they are called, but are more into the field of social engineering, are also a major problem, and in 2021 alone, more than $14 billion worth of crypto was stolen, as reported by Time. Someone out there is after your funds, which is why security is of the utmost importance.
Your crypto wallet is your treasury, your virtual fortress on the blockchain. Let’s explore its variations and how to protect them.
Custodial vs. non-custodial crypto wallets
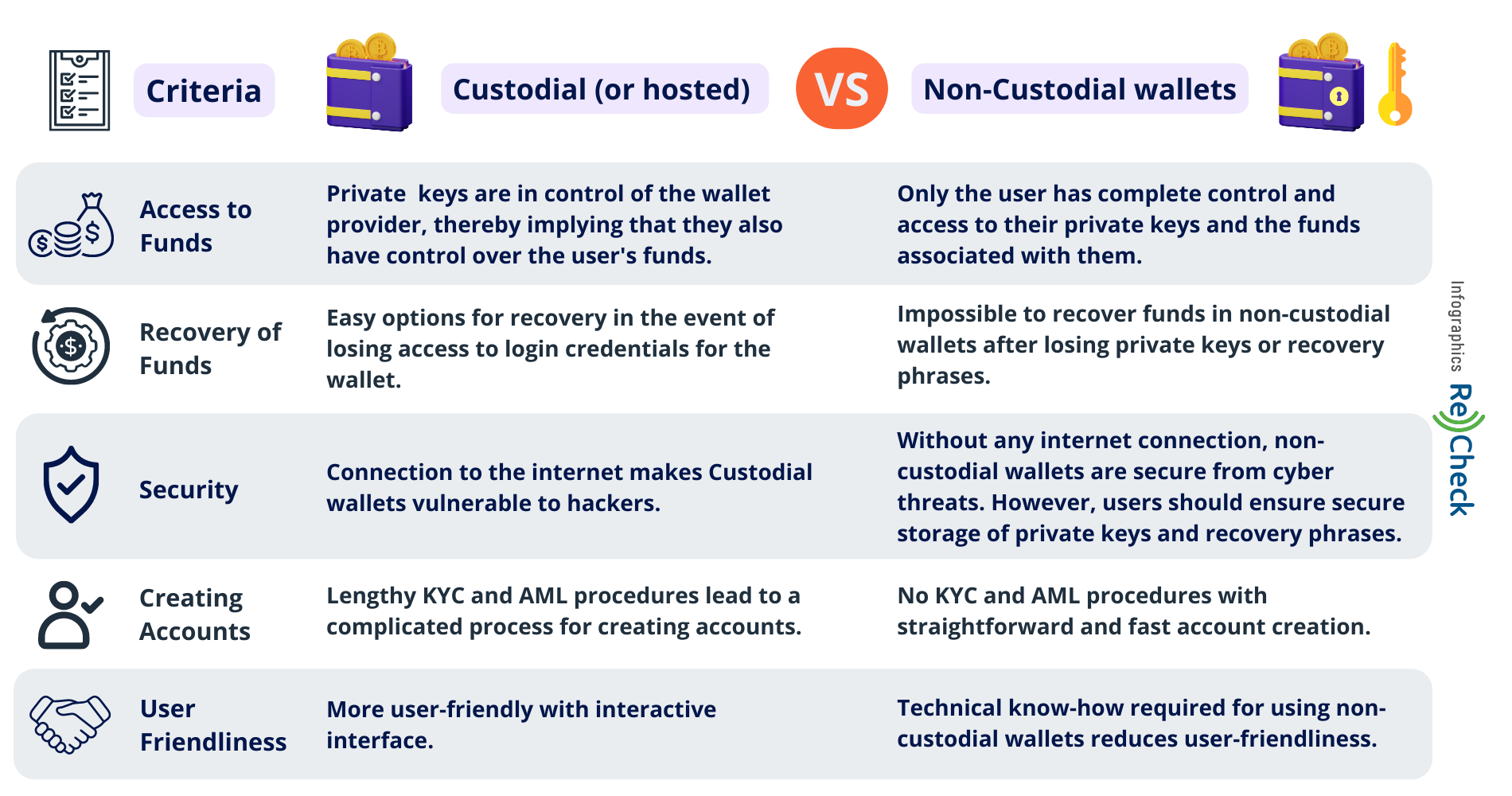
Your wallet is where your crypto journey begins. It is the first thing you acquire, and it is the foundation you build your portfolio, so securing it is of the utmost importance. The first choice one must make when it comes to crypto wallets is this: custodial or non-custodial.
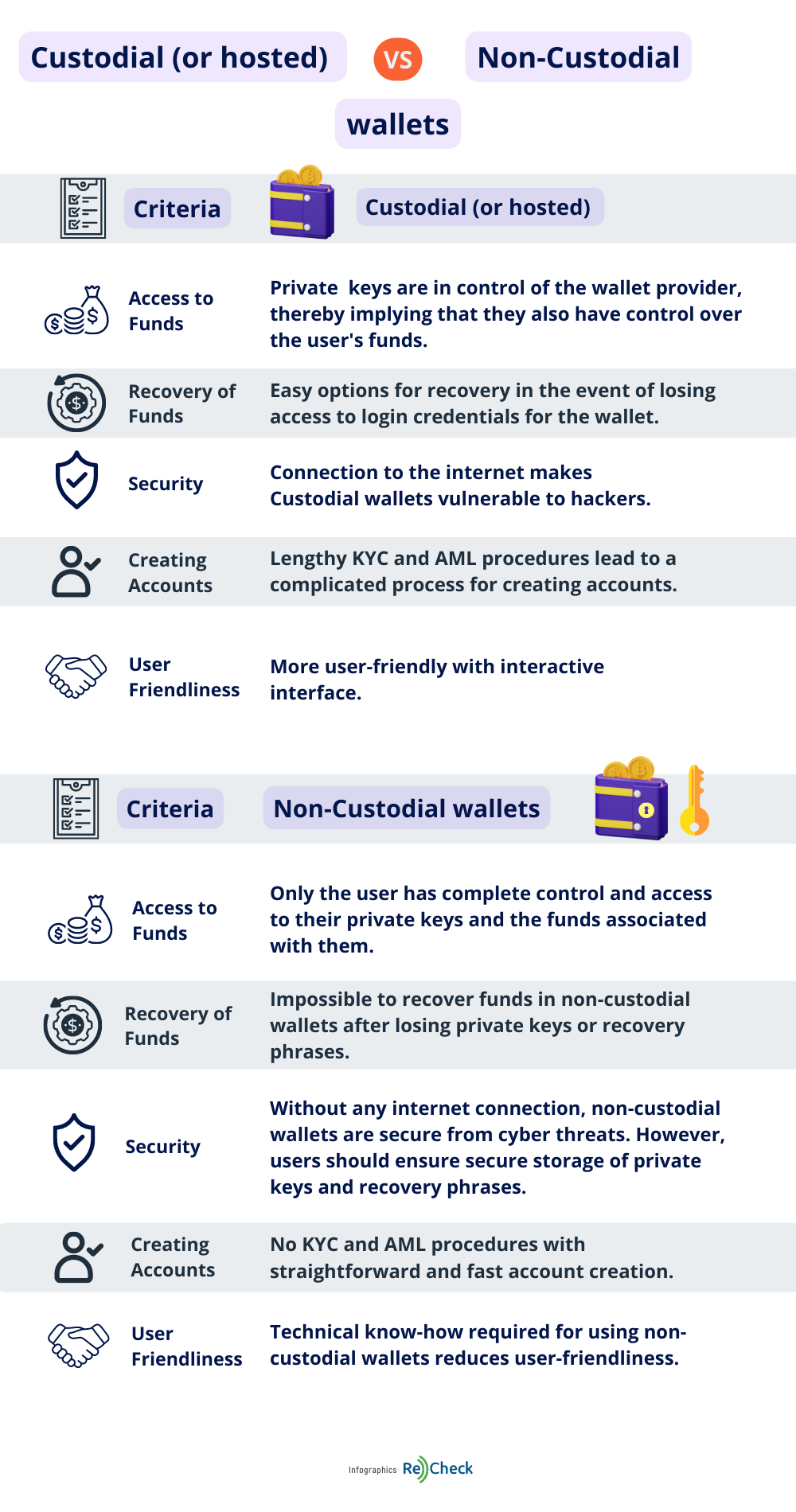
A custodial wallet means that, while having access to it and the funds stored inside, you do not actually own the keys to the treasury, so to speak. A custodial wallet is a wallet that is hosted by a third party – most often a centralized exchange – which in turn owns the cryptographic keys that allow access to the stored funds. You have undoubtedly heard the expression “Not your keys, not your wallet”, and that is very much true – yes, you maintain access to it, but the third party may decide at any point that you are, for example, in violation of their terms and conditions, and can therefore lock you out or freeze your funds with no warning.
A custodial wallet beats the entire purpose of crypto – decentralization, and privacy, with your private keys handled by a centralized organization.
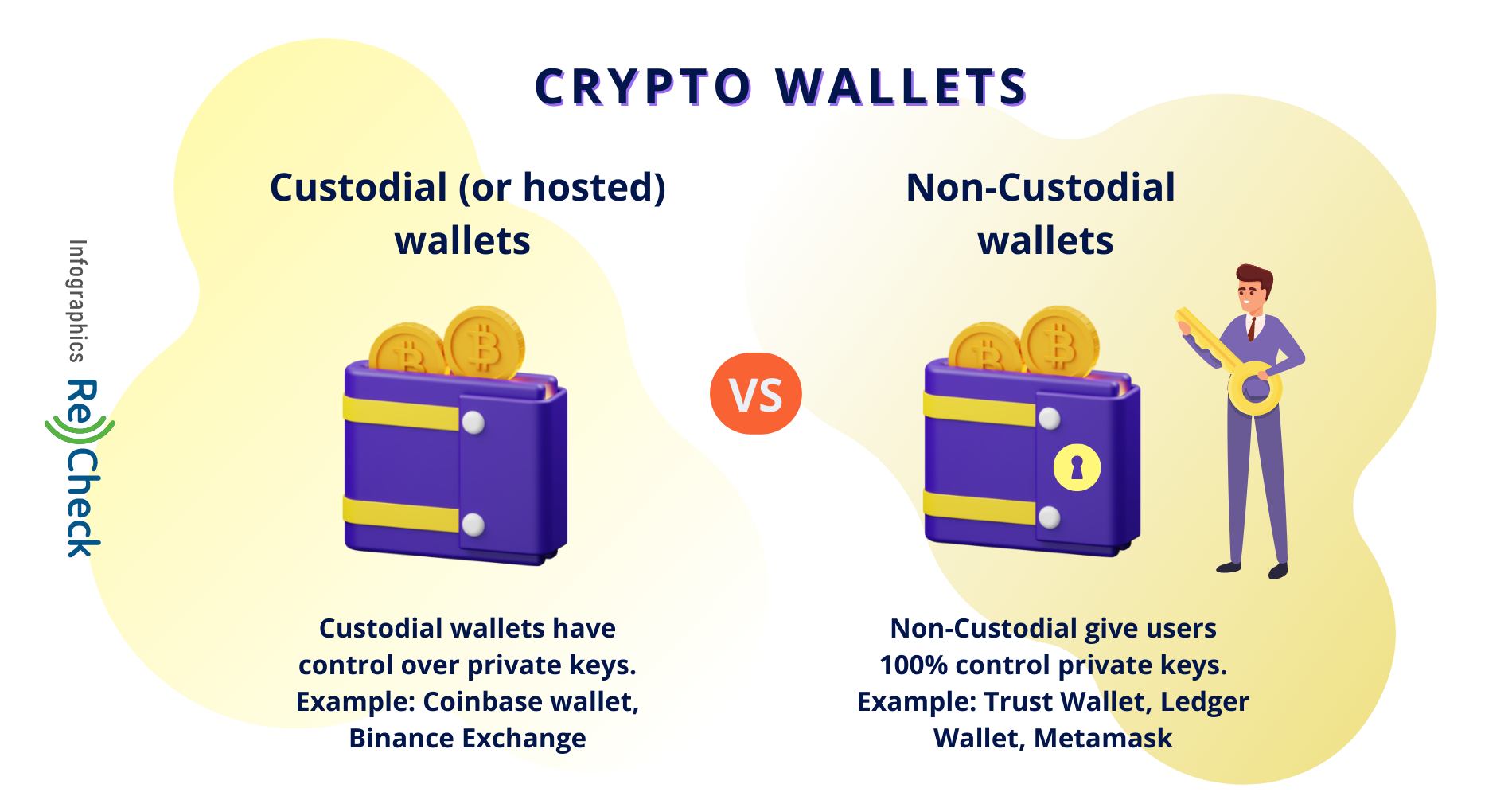
A non-custodial wallet, on the other hand, places control in the hands of the user, honoring the Bitcoin legacy of empowering the everyday investor. Non-custodial wallets are hosted on your desktop computer, mobile device, or even browser, eliminating the need for a centralized entity. Non-custodial crypto wallets can be hot and cold. A hot wallet is simply a wallet you have installed on a device, while a cold wallet (also called a hardware wallet) is a physical device that needs to be connected to a computer only when transactions are in order.
Cold crypto wallets are thus the most secure form there is, and even malware-infested computers cannot compromise them because the transactions are being signed offline inside the wallet before being sent to the blockchain.
With non-custodial wallets, you are the owner of your private keys and all funds stored inside; therefore, the responsibility to secure your holdings is entirely up to you. This is both a blessing and a curse – non-custodial crypto wallets eliminate the third party from the picture but can be somewhat stressful to manage. If the wallet is somehow lost or destroyed, or its password is forgotten, and you have not taken precautions to somehow reinstate it, then the funds are lost forever and cannot be redeemed. There are some easy and practical solutions to remedy that, which any investor should abide by in order to protect their assets.
Are you looking for ultimate security and privacy in a data exchange?
Crypto Wallet Security 101
All non-custodial wallets must be protected by a strong and unique password – one that you do not use in any other accounts. Use a random sequence of numbers, letters, and symbols, and aim for a length of at least 30 characters. It might seem like overkill, but it is better to overdo it than wake up one day to find your funds missing. Do not write your password down on your device no matter what – keep it strictly on paper and never share it with anyone.
And remember: non-custodial wallets do not keep your password for you, and you cannot reset or change it – if you lose it, it is gone, and with it, your access to funds. There is, however, a backup solution.
All non-custodial wallets have what is called a seed phrase, one of the first screens you see when installing a new wallet on your device. A seed phrase, also called a mnemonic phrase, is a string of randomly generated words, which can be used to reinstate your wallet on any device in the worst-case scenario of it being lost or destroyed, or if you lose your password. Your seed phrase is unique, no one else has access to it, and if you lose it, it is gone forever. The seed phrase is where things end.
Never, and this cannot be overstated enough, never store your seed phrase on any device, and do not take pictures of it.
Some types of malware are specifically designed to look for .txt or .doc files with 12, 18, or 24 words inside, which is the most common length of a seed phrase. If you store your phrase on a device, your holdings are compromised from the first day. Do not use cloud storage or any other online storage services you may have – if your seed phrase is kept on anything that has electricity and a connection to the internet running through it, your assets are in danger.
Write your seed phrase on a piece of paper, make a copy, and lock it up in two different places – it is the only way to be safe. While doing that, and if you really want to be cautious, make sure nobody is watching and that you are away from windows and cameras. Never share your mnemonic phrase, never upload it, never send it – if anyone has access to it, they can “recreate” your wallet from anywhere in the world, and they don’t even need your device to do it.
If this seems like too much work, a custodial wallet might be a better option, although you will also have to take good care of your account there and be extra careful. The password still needs to be unique and strong, and two-factor authentication (2FA) is necessary in order to increase your chances that, even in the case of a malicious attack, your account will remain secure.
Apart from that, whitelisting addresses is a very good idea, and most centralized exchanges offer it as a service. When you whitelist, you can only transfer funds to the whitelisted address while still having to use 2FA to sign the transaction. This is another layer of security that can be vital in case of an attack. 2FA has its critics, though, and sim-swapping, where an attacker highjacks your phone, remains a danger. That’s why you could always use a third-party authenticator, which provides you unique codes every few seconds that authenticate transactions.
Another important thing to keep in mind is to always be careful what websites you visit from the device that has your wallet. Malicious software could be anywhere, and you don’t know how it could affect your device. One famous example is that of key loggers – a type of malware that records all input done on your keyboard and can be used to steal login data and passwords. A good way to go around this is to use the on-screen keyboard, entering your password with a combination of hard keys and virtual keys.
It is, of course, also a good thing to keep your antivirus software updated and to scan your device at least once per week. In order to be safe, you could also carry out a quick malware scan every time before accessing your wallet.
And last but definitely not least – never let your guard down. With new security, methods come new exploits, and staying up to date with the latest developments is always a good call. This could make all the difference.